
Interested in SOC Services for Darktrace?
Enhance your cybersecurity posture and embrace the future of threat detection with Cyberseer's SOC services for Darktrace.
A website malware attack is proving to be a popular choice with criminals. Attackers increasingly exploit web servers, the websites they host, and the people who use them. Over the last few years, there has been a steady growth in the number of website vulnerabilities, with more than 75 per cent containing unpatched vulnerabilities, of which 15 per cent were deemed critical1.
The two most popular methods criminals use for the mass distribution of malware are malicious spam and web browser pop-ups. Malicious spam is mainly in the form of bulk emails or phishing campaigns, requiring the user to click on the infected attachment. However, web browser pop-ups happen behind the scene without a user’s knowledge.
This technique is called an Exploit Kit and they take advantage of client-side vulnerabilities. With Java, Adobe Reader and Flash present on 99 per cent of computers, 99 per cent of users are also vulnerable to Exploit Kits3. Full access to your computer can be given to a hacker in one click.
In the explanation below we discuss an example recognised from a recent malware campaign detected by Cyberseer’s Security Analysts within an organisation’s environment. Our Analysts determined the nature of the attack and counselled the organisation to take appropriate action.
An Exploit Kit can be defined as a framework that uses exploits to take advantage of vulnerabilities in browser-based applications, which allows code to be planted to infect a device with malware without the user’s knowledge. Exploit Kits are increasingly being found inserted and hidden within compromised websites.
A typical Exploit Kit has three phases in its chain of infection:
By itself an Exploit Kit is not effective, it is part of a larger ecosystem containing actors and campaigns. An actor is an individual or criminal group behind a piece of malware and a campaign is a system that consists of an Exploit Kit plus an infrastructure that directs victims to that Exploit Kit or malware.
In its simplest form, the chain of infection for a campaign looks like this:
From beginning to end, each website malware attack can be broken down into 5 common steps, with an infection happening in less than a second:
A drive-by download involves downloading malicious code by just visiting a web page. A drive-by download happens automatically without any user interaction or knowledge. The most used type of drive-by download is the technique of injecting malicious JavaScript into a legitimate website that then redirects the user’s browser to a malicious website that hosts malicious code.
In this example, you can see the genuine website www.thatauditguy.com has been compromised with malicious code and is redirecting the user.
Once the code is loaded by the browser, the unsuspecting user is then redirected to an exploit kit hxxp://gikida.xyz/wwkdaimiiemercdf-... shown below in the embedded code.
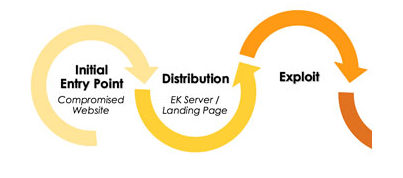 This phase of a web attack is where the actual browser exploit to be used is downloaded, usually from the website that is being used to host the malware. These kits execute various exploits against common or previously unknown vulnerabilities in web browsers and plugins such as Flash, Silverlight, and Java.
This phase of a web attack is where the actual browser exploit to be used is downloaded, usually from the website that is being used to host the malware. These kits execute various exploits against common or previously unknown vulnerabilities in web browsers and plugins such as Flash, Silverlight, and Java.
Once a user’s browser has landed on a website hosting an exploit kit, the kit will proceed to load and execute files that target vulnerabilities relevant to the victim’s computer.
These vulnerabilities will be based on information available from the user’s browser, such as information extracted from their user agent. In this instance, you may not have installed the latest Flash updates, which results in the Flash plugin in your browser being vulnerable, giving the exploit kit a way into the system without the user knowing.
Once the attacker exploits an application vulnerability to gain some control over the computer, the next step in the attack is to download a payload to infect the system. This is part of the malware which performs the malicious action. Infection types include variants of Ransomware, information-stealing tools or even Remote Access Trojans (RATs).
The example below details a GET request that drops the binary file or payload into your system with Ransomware.
The final stage of an attack is where the malware begins to carry out the malicious activities it has been programmed to do. The screenshot below shows the Ransomware communicating its status back to its command & control host via POST requests. In the case of Ransomware, the final goal will be to encrypt the victim’s files and request payment for the decryption key.
Other malware may steal confidential data such as usernames and passwords, or financial information (online banking credentials, credit card details etc.) or, provide the attacker with a remote access foothold to enable further lateral movement into an organisation to target specific data.
Each stage of the website malware attack life cycle presents an opportunity for an attack to be detected. Advanced security technologies such as Darktrace look for anomalous behaviour rather than signature matches. When combined with skilled in-depth analysis it is possible to proactively identify different stages of an exploit’s chain of infection:
Suspicious domains
Communication with Command and Control (C2) infrastructure
POST requests to rare external destinations
File downloads – e.g. flash or java download
Further analysis of contextual packet captures allows an analyst to identify further actions of delivered malware.
A machine-learnt behavioural approach to security can detect threats ahead of other traditional solutions, allowing a faster response to potential breaches. Security technologies that require signatures and blacklists to be updated will always be one step behind the attackers and will never be able to detect new unknown threats in real-time.
Keeping up-to-date with the latest technology and solutions to protect against website malware attacks and safeguard your financial and personal information is paramount. By regularly assessing your website for vulnerabilities and malware, and educating all users on basic good security practices, you can reduce your risk of being compromised.
Sources: [1] Heimdal Security [2] Symantec ISTR [3] SecurityWeek