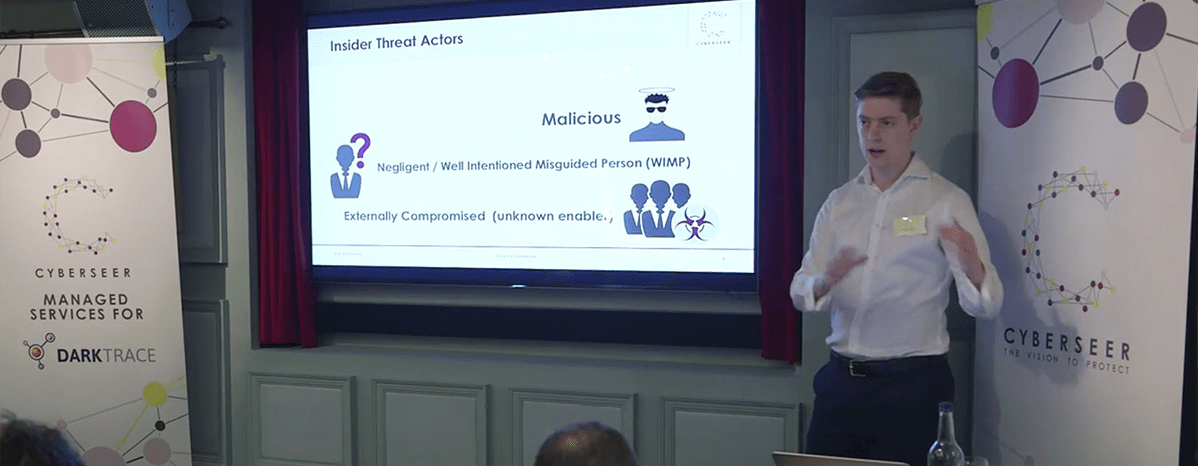
We had a full house at the Insider Threat breakfast briefing. For those who couldn’t attend and missed out on our speakers discussing who are the “insiders”, how they operate, what motivates them and what threats they pose to information systems, here’s some video footage:
- Highlights from the Insider Threat Breakfast Briefing
- What is Insider Threat?
- Insider Threat in Context
- Detecting Insider Threat – Cyberseer demonstrates how they detect ‘insider threat’ using Darktrace
‘Insider threat’ is a prevalent successful attack vector in an organisation. Did you know? It can take an average of 240 days to detect an insider threat and an average of 70 days to resolve that threat. So in total, we’re looking at an entire year of potential operational costs and other costs incurred due to malicious insiders.
At this briefing, Cyberseer explained how new and emerging tools from Darktrace and forensic analysis from the Cyberseer team can support organisations with the mitigation of the insider threat problem. For more information, read our white paper – Detecting Insider Threat.