
How Cyberseer Detect Burp Suite using Darktrace
This article explains how Cyberseer detects the use of the Burp Suite framework in network traffic flow using Darktrace technology.
Technical support and remote access scams aren’t exactly a new concept, they have been observed since as early as 2008. The premise is simple, the scammer cold calls the victim posing as a legitimate-sounding third-party, with a name such as “Microsoft” or “Windows Technical Support” and offers to resolve issues such as malware being detected on the user’s computer.
The next step is to get the victim to download a remote assistance tool essentially giving the scammer free access to the machine and everything on it. From here the scam typically moves towards trying to coerce the victim into paying for unneeded “support” services, however, with the scammer having free reign on the user’s machine there’s nothing stopping them from stealing sensitive documents or files. In a business environment, the scope of sensitive documents available increases dramatically.
You may be thinking to yourself that there’s no way anyone would ever fall for this… In 2017, the Internet Crime Complaint Center (IC3) received approximately 11,000 complaints related to technical support scams. The claimed losses amounted to nearly $15 million.
This article focuses on a recent threat discovered by Cyberseer that involved the download of a tool commonly seen with technical support scams and the eventual upload of data through the use of this remote assistance tool.
Cyberseer deploys advanced threat detection solutions as part of its managed security services, across a range of businesses and industries. By leveraging Darktrace’s Enterprise Immune System, a machine learning and mathematics-driven cyber defence tool, Cyberseer Analysts were able to rapidly detect and alert the customer to the breach and prevent further data upload and network disruption.
The following section will look at how unsupervised machine learning detected this remote assistance scam in action.
The initial download of the remote assistance tool from the domain supremofree[.]com located at 151.80.237.21 is immediately detected as a suspicious download from a domain the device has never previously connected to:
Wed Jun 6, 13:58:30 <strong>laptop1.bluetick.com</strong> breached model <strong>Anomalous File / EXE from Rare External Location</strong>
Wed Jun 6, 13:58:29 File Transfer (EXE) — FileTransfer::Exe file found with filetype (application/x-dosexec) [80]
Wed Jun 6, 13:58:18 <strong>laptop1.bluetick.com</strong> connected to <strong>151.80.237.21</strong> [80]
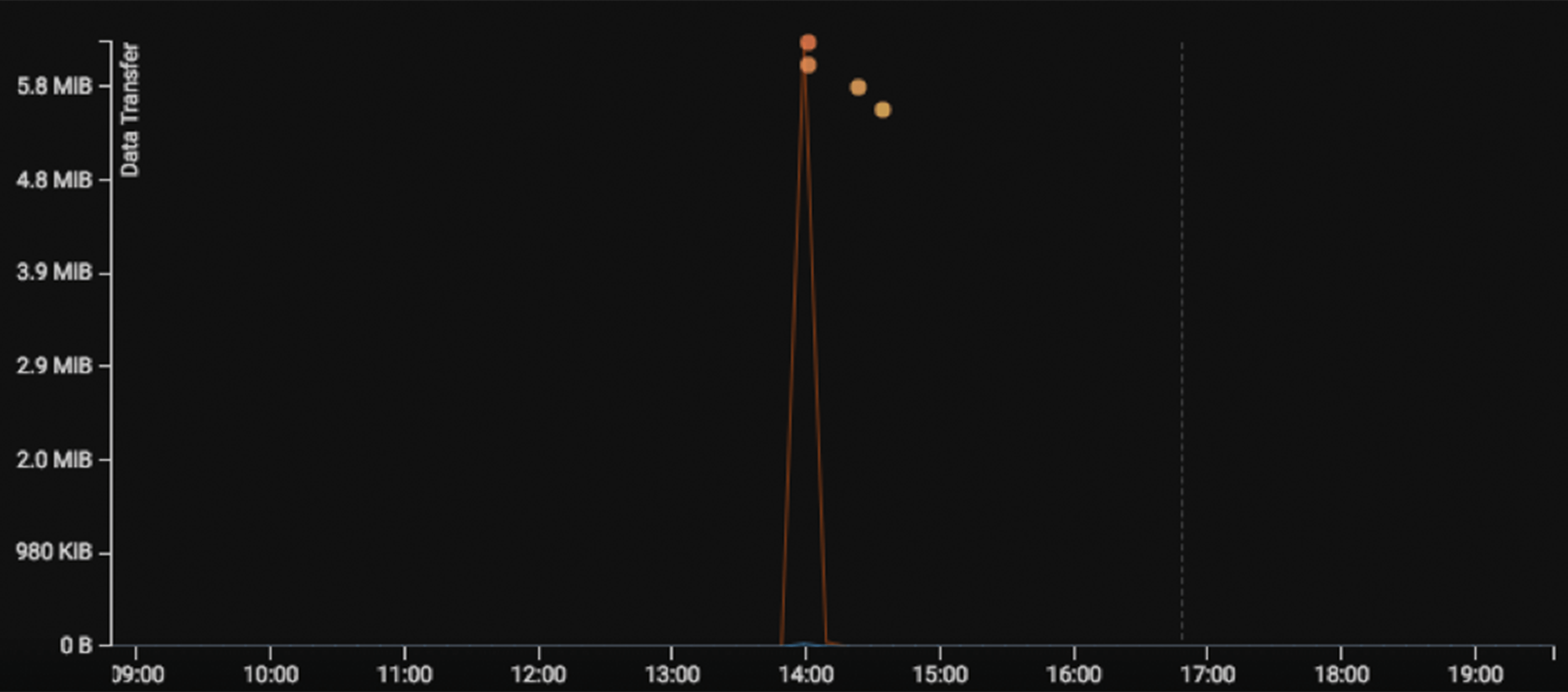
Once the victim has installed the remote assistance tool on their machine, the machine is seen with a new user agent and instantly begins sending HTTP POST requests to the domain supremogw*[.]nanosystems[.]it. Throughout the duration of this activity, approximately 6,000 connections were seen.
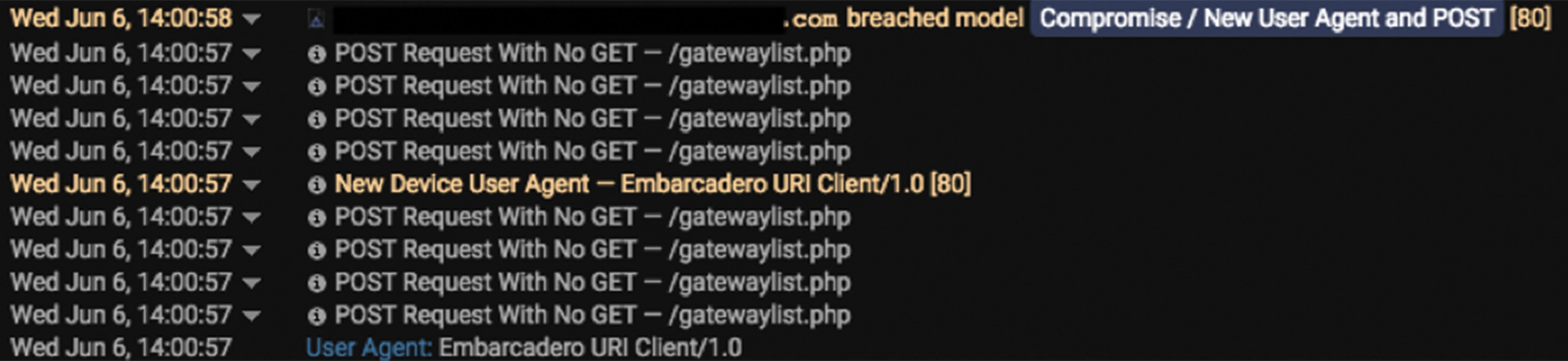
06/06 14:20:25 http 10.0.0.1 56804 136.243.249.218 443 - - <strong>supremogw19.nanosystems.it</strong>
128 <strong>/$rdgate?ID=EA13F2C174C64153BCA2381D9297A4A8</strong> [HOST,CONTENT-LENGTH] 75 33 1.1 OK <strong>POST</strong> 200
06/06 14:20:31 http 10.0.0.1 56804 136.243.249.218 443 - - <strong>supremogw19.nanosystems.it</strong> 130
<strong>/$rdgate?ID=EA13F2C174C64153BCA2381D9297A4A8</strong> [HOST,CONTENT-LENGTH] 75 33 1.1 OK <strong>POST</strong> 200
As the number of HTTP POST requests increases, so does the amount of data being externally transferred:
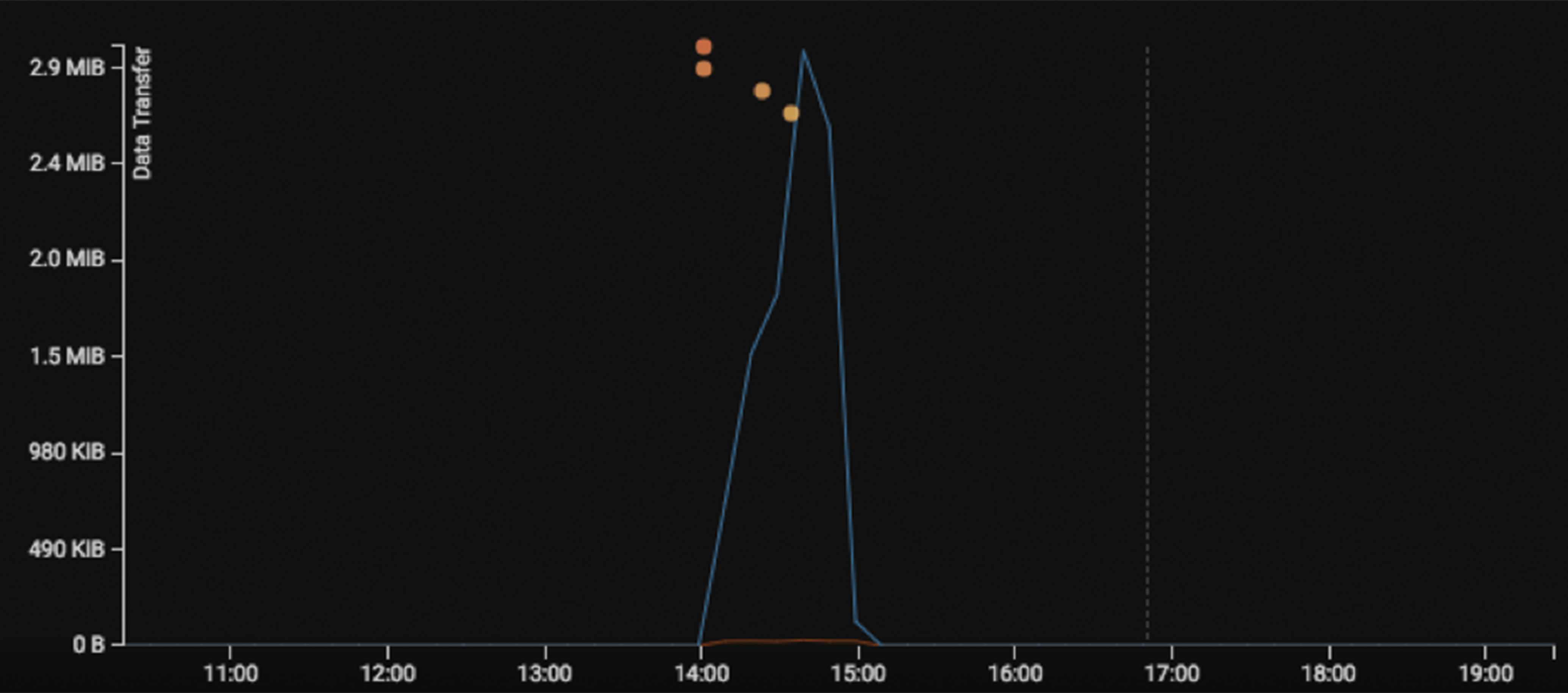
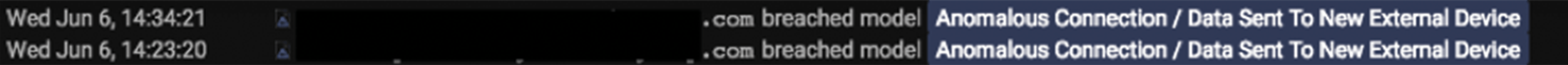
This highly anomalous behaviour marks a sharp departure from the user's normal ‘pattern of life, making it very easy to detect as data is being sent to a new external device:
During this activity, approximately 52 MiB of data was uploaded.
This scenario highlights how traditional signature-based approaches are not enough to adequately defend a network against constantly evolving, new unknown threats. The Darktrace technology does not require any prior knowledge of threats or need to update signature definitions.
As shown above, a machine-learnt behavioural approach to security can detect threats ahead of other traditional solutions, allowing a faster response to potential breaches. Security technologies that require signatures and blacklists to be updated will always be one step behind the attackers and never be able to detect new unknown threats in real time.
Cyberseer’s threat detection and analysis service bridges the gaps in an organisation’s cyber defence system. Having the ability to detect and understand the severity of internal and external threats provides effective threat mitigation.
Understanding your organisation’s threat score and dealing with live issues early, decreases incident response times and significantly reduces the risk of cyber damage.

This article explains how Cyberseer detects the use of the Burp Suite framework in network traffic flow using Darktrace technology.